CiscoFirewallTroubleShootingIssues
Friday, 28 September 2012
Wednesday, 29 August 2012
CCNP Security 642-617
Here’s a link to my study notes in bullet
form about topics I found interesting / useful in everyday tasks: 642-617 exam.
I’ve also found mindmaps to be a very useful tool in my studies.
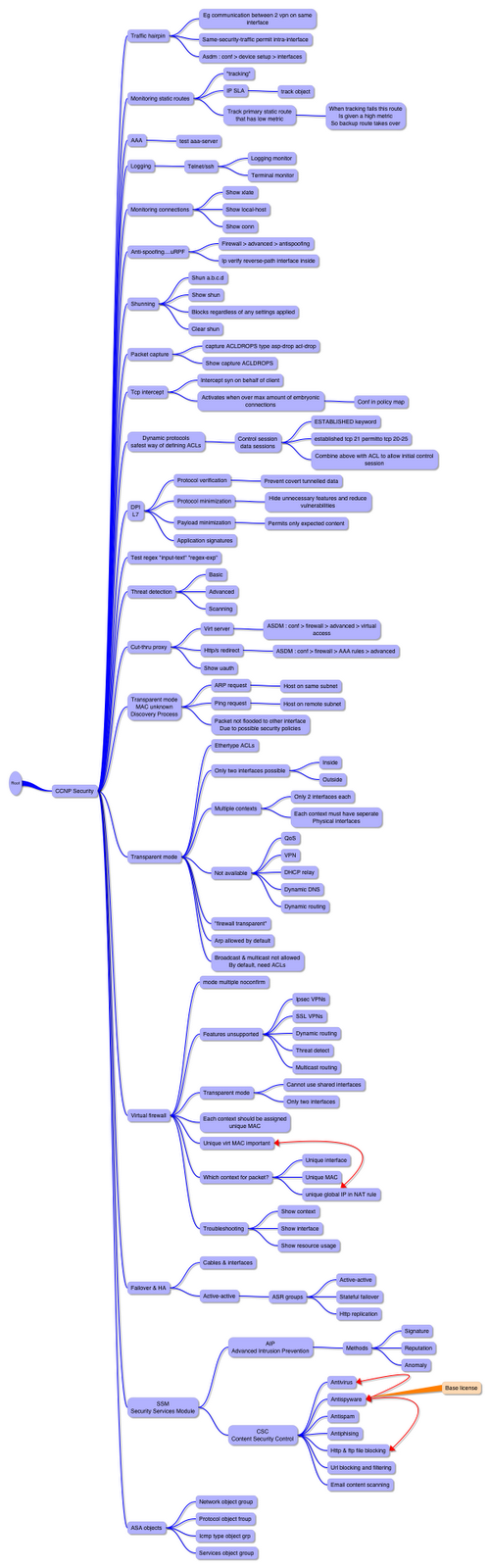
I’ve also found mindmaps to be a very useful tool in my studies.

Wednesday, 1 August 2012
Activate ASDM as GUI Interface for Cisco ASA/PIX Firewall
pixfirewall> enable
Password:
pixfirewall# configure terminal
pixfirewall(Config)# interface ethernet1
pixfirewall(Config-if)# nameif inside
pixfirewall(Config-if)# ip address 192.168.1.1 255.255.255.0
pixfirewall(Config-if)# no shutdown
pixfirewall(Config-if)#
Password:
pixfirewall# configure terminal
pixfirewall(Config)# interface ethernet1
pixfirewall(Config-if)# nameif inside
pixfirewall(Config-if)# ip address 192.168.1.1 255.255.255.0
pixfirewall(Config-if)# no shutdown
pixfirewall(Config-if)#
Activate ASDM and enable http server.
pixfirewall(Config)# asdm image flash:/asdm.bin.
pixfirewall(Config)# http server enable.
pixfirewall(Config)# http server enable.
Open a connection for your PC. Example your pc IP address is 192.168.1.2
pixfirewall(Config)# http 192.168.1.2 255.255.255.255 inside
Make sure all your config running properly.
pixfirewall(Config)# show running http
http server enabled
http 192.168.1.2 255.255.255.255 inside
pixfirewall(Config)#
http server enabled
http 192.168.1.2 255.255.255.255 inside
pixfirewall(Config)#
Now your Cisco ASA/PIX can be access from your PC.
Make sure your PC and Firewall has connected and open your web browser then enter this address https://192.168.1.1/admin
ASDM for Firewall Troubleshooting
ASDM for Firewall Troubleshooting
A client recently contacted me regarding a problem he attributed to his Cisco ASA firewall. The problem preventedencrypted email traffic out on the Internet. The encryption used to access Gmail's servers was TLS / STARTTLS on portTCP 587.
For this troubleshooting session, I used ASDM (ASA graphical tool for 550x firewalls). First, I conducted a 'Packet Tracer'to source IP 172.27.0.32 (server issuing the e-mail). A packet trace simulates the forwarding of a data packet, with the TCP / UDP port of your choice, and with the source and destination addresses of your choice. In this instance, the destinationsmtp.gmail.com is resolved to 74.125.93.109 and TCP port of destination was 587. All this from the COR interface (inside).As depicted in the following figure, the packet passed all the checks between the interface COR (inside) and PUB(outside). Green check marks indicate success for each phase, like ACLs, NAT, etc.
The above results confirms that type of traffic is allowed through the firewall. At this point, I began suspecting the client's Windows server.
ASDM provides a tool called 'real time log viewer'. It lets you view the logging in the ASA in real time (this feature has been available forever), but in addition you can filter by IP address, source / destination port, etc.. There is even an option'Build Filter' which helps to build the filter conditions, similar to Wireshark. The following figure illustrates severalconnection attempts to smtp.gmail.com (IP 74.125.93.109) with the server's source IP (172.27.0.32) to TCP ports 80, 58,586, 587. All these connections passed through the firewall, except for port 587. At that moment, I concluded that port 587was blocked at the client's server. After investigation, I found that a newly installed anti-virus package denied certain typesof traffic. I circumvented the rule in the anti-virus software and traffic for TCP port 587 began to forward, as observed in thelast logging entry (log entries are listed in descending chronological order).
Conclusion
I have often witnessed connectivity problems in client servers due to Windows Firewall service. Recently, anti-virus softwarecaused a similar connectivity problem. ASDM real time log viewer added value in the troubleshooting process. If you are using a Cisco ASA firewall, I recommend installing ASDM on at least one of your Windows servers sitting behind thefirewall. This tool is free and easy to use.
I have often witnessed connectivity problems in client servers due to Windows Firewall service. Recently, anti-virus softwarecaused a similar connectivity problem. ASDM real time log viewer added value in the troubleshooting process. If you are using a Cisco ASA firewall, I recommend installing ASDM on at least one of your Windows servers sitting behind thefirewall. This tool is free and easy to use.
Subscribe to:
Comments (Atom)

